The new Panda Free Antivirus provides the easiest-to-use and most intuitive protection for your computer. Install it and forget about viruses, spyware, rootkits, hackers and online fraud. Enjoy real-time protection against the latest malware threats.
Touch N Go is a Biometric Framework (SDK or API) that allows programmers to integrate fingerprint recognition in their application with just FOUR lines of code. It supports multiple database (Oracle, MS SQL, MySQL Enterprise, Sybase, and IBM DB2, etc.) and multiple programming languages (C/C++, C#, .NET, VB.NET, F#.NET, Java, Ruby, Delphi, etc.). It also supports most fingerprint scanners available in the market.
This simple program will help to find password to zip file, if the password is lost. A distinctive feature of this handy tool is the high speed of its work, which does not depend on the number of files included in the zip file. The utility includes a number of settings, including the ability to specify the range of the password length and the type of its constituent characters.
Word Password Recovery Lastic introduces a unique approach to cracking Microsoft Word passwords. Unlike other tools, it allows cracking passwords not only in a single document, but in multiple documents at once. The program flawlessly cracks passwords to open and to modify, document protection passwords and VBA passwords. Automatic search discovers password protected documents on your disk that you can crack with a single click.
AutoKrypt is an encryption software designed for automation that will automatically encrypt or decrypt files and folders. AutoKrypt's encryption methods include password based, public and private key, secret key, OpenPGP password, OpenPGP public and private key.
Enterprise software to instantly recover your lost or forgotten mail passwords from all versions of Outlook. It also helps you to remove stored email passwords to prevent it from being stolen by hackers/virus/ransomwares.
Oracle Password Recovery and Auditing Software
Chili Antivirus is the indispensable anti-virus software that protects against virus attacks. It is based on an award-winning technology as rewarded by AV-TEST with the accolades of having both the ''Best Protection'' for three consecutive years, and also ''Best Performance'' regarding its system speed. Incredibly easy to use, and secures your Mac with a single click of the button.
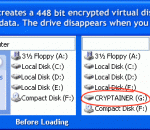
Cryptainer USB Encryption Software allows to create a 'stand-alone' or a 'portable' install on External Drive such as USB Flash Drive. Cryptainer USB can be run directly from the device without having to be installed on the host computer. No matter where you are, you can easily carry your important data (stored within an encrypted drive) with you. Cryptainer USB prevents data leakage from theft and lost of USB drive or any portable drive.
Paradox Recovery allow to find the lost password for Paradox tables. An application don't use any external libraries (no BDE, no ODBC, no ADO etc) and you may run this tool on any computer without any additional setup/install. You may customize the brute-force or dictionary search process for entire password with extended options. All versions of Paradox tables and all file kinds (data, indexes etc) supported.
Keeper is a safe and secure way to store all of your secret passwords, notes, website logins and other top secret personal information on your laptop or desktop computer. Keeper's military-grade encryption (128-bit AES) allows data to be safely and securely stored on the hard drive of your computer, not online.
Iperius Backup является одним из лучших бесплатных ПО для резервного копирования, имеет также коммерческую версию с широким набором передовых функциях резервного копирования. Бесплатная версия Iperius Backup позволяет проводит резервное копирование на любые носители информации, как NAS, внешние диски USB, носители RDX и компьютеры в сети. Включает в себя полнофункциональный планировщик заданий и функцию отправки e-mail. Поддерживает сжатие zip без ограничения в размере файлов, инкрементальный бэкап, аутентификацию в сети и запуск внешних скриптов и программ.
Антивирус Касперского защищает вас от фишинга и вредоносных сайтов, которые вы иначе бы не знать, пытаются украсть у вас. В то же время Kaspersky Security Network позволяет компьютеру сообщить, когда он обнаруживает угрозу, которая не видели раньше. Все 250 миллионов пользователей Kaspersky воспользоваться нашей совокупных знаний! Kaspersky функции включают в себя: защищает от вирусов, троянов, червей, шпионских программ, adware сканирование файлов, электронной почты и Интернет трафика защищает мгновенных посыльных защищает от неизвестных угроз анализирует и закрывает уязвимости Internet Explorer отключает ссылок на зараженные сайты / фишинговых сайтов глобальной угрозы мониторинг (Kaspersky Security Network) блоки всех типов клавиатурных шпионов автоматическая база данных обновления Бесплатные технической поддержки Примечание: это 30-дневный коммерческие суда.